Network protocols
Application layer- End-user applications like web browsers and email clients operate at the application layer. It offers protocols that let computer programmes transmit and receive data and provide users useful information.
- Several illustrations of application layer protocols include:
-FTP, or File Transfer Protocol
- DNS, or domain name system
-SMTP, or Simple Mail Transfer Protocol, and
-POP, or Post Office Protocol.
Application Layer Protocol
HTTP
- Hyper Text Transfer Protocol is known as HTTP.
- There are involved papers or files because of the hypertext. These may include text, graphics, pictures, videos, or other types of media. The term "Transfer" refers to the ability of files to be transferred between networked devices over the World Wide Web. The term "protocol" refers to a set of regulations controlling network communication.
- Communication between web clients and servers is crucial to the WWW.
- Sending and receiving HTTP Requests and Responses is the primary method of communication between client computers and web servers.
HTTPS
- The Secure Socket Layer (SSL)/Transport Layer Security (TLS) protocol and the Hypertext Transfer Protocol (HTTP) are combined to form the Hypertext Transfer Protocol Secure (https).
- TLS is a widely used authentication and security mechanism for Web servers and browsers.
FTP
- "File Transfer Protocol" is the abbreviation for a set of guidelines that control how computers move files from one system to another via the internet. FTP is used by businesses to transfer data between computers, while websites utilise it to upload and receive files from the servers that host their websites.
- FTP operates by establishing two connections between the machines that are attempting to interact. The data transfer is handled by one channel, while the other is used for the orders and responses that are transmitted back and forth between the two clients. The interacting computers, servers, or proxy servers employ four instructions during an FTP transaction. The following are examples: "send," "get," "change directory," and "transfer."
- FTP has three main modes for file transfers: block, stream, and compressed. FTP may manage data in a string of data without any boundaries by using the stream mode.
DNS
- The phonebook of the Internet is the Domain Name System (DNS). Domain names like espn.com or the new york times.com are used by people to access information online.
- Through Internet Protocol (IP) addresses, web browsers may communicate. In order for browsers to load Internet resources, DNS converts domain names to IP addresses.
- Each Internet-connected device has a distinct IP address that other computers may use to discover the device.
- The requirement for humans to memorise IP addresses like 192.168.1.1 (in IPv4) or more complicated modern alphanumeric IP addresses like 2400:cb00:2048:1::c629:d7a2 (in IPv6) is eliminated by DNS servers.
SMTP
- The Simple Mail Transfer Protocol (SMTP) is a set of rules for communication that enables applications to send electronic mail over the internet.
- Based on email addresses, it is a programme used to deliver messages to other computer users.
- Between users using the same or other computers, it offers mail exchange, and it also supports:
-One message may be sent to one or many recipients.
-Messages can be sent using text, audio, video, or graphics.
-The communications may also be sent through networks other than the Internet.
- Setting up communication rules between servers is the major usage of SMTP. The servers can identify themselves and state the type of communication they are attempting to carry out. They also provide a method for dealing with issues like a wrong email address. For instance, if the destination address is incorrect, the receiving server will respond with some sort of error message.
POP
- Post Office Protocol is the full name of the protocol. SMTP is employed as a message transport agent, as is well known. When a message is sent, SMPT is used to transfer it from the client to the server, where it is then sent to the receiving server.
- However, the Message Access Agent assists in retrieving the message from the receiving server. POP3 and IMAP are the two types of protocols that are included in the Message Access Agent.
TELNET
- A standardised way for interacting with terminal devices and terminal-oriented operations is provided by the Telnet Protocol (TELNET).
- Programmes that emulate terminals and let you connect in to distant hosts frequently utilise TELNET. TELNET, however, may also be used for inter-process communication and terminal-to-terminal communication.Other protocols (like FTP) can also establish a protocol control channel using TELNET.
- In the tn, telnet, or tn3270 user commands, TCP/IP implements TELNET. There is no TELNET API provided by the telnetd daemon.
Transport Layer
- In the TCP/IP paradigm, the Transport Layer is the second layer, while in the OSI model, it is the fourth layer.
- In order to convey messages to a host, it is an end-to-end layer. It offers a point-to-point connection between the source host and destination host rather than a hop-to-hop connection, which enables it to deliver the services consistently. This is why it is known as an end-to-end layer.
- In the Transport Layer, a segment is the basic unit of data encapsulation.
- From the perspective of the sender, the transport layer takes data (messages) from the application layer, splits the data, adds the source and destination ports to the header of each segment, and sends the message to the network layer.
- The transport layer takes data from the network layer, segments it, reads its header, determines the port number, and then passes the message to the correct port in the application layer.
TCP
- Layer 4 protocol TCP sends out duplicates of any lost packets and offers acknowledgement of the received packets.
- Although it is superior to UDP, these functionalities come at an added overhead. Application protocols like HTTP and FTP make use of it.
- The synchronisation, synchronisation acknowledgment, and final acknowledgement phases of the TCP handshake are as follows:https:
- Although it is a layer 4 protocol like TCP, UDP does not offer packet acknowledgment.
- It is therefore unreliable and is dependent on protocols at higher layers for the same. However, compared to TCP, it is simpler, more scalable, and has less overhead.
- Both voice and video streaming employ it.
Differences between TCP and UDP
link:https://www.codingninjas.com/studio/library/tcp-vs-udpl
ARP
- Address Resolution Protocol is referred to as ARP.
- It is utilised to link the MAC address and IP address.
- The MAC address encoded on the NIC identifies every device connected to the network. As a result, we may state that devices on a local area network require the MAC address in order to communicate. It is simple to modify a MAC address.
- For instance, when a machine's NIC malfunctions, the MAC address changes but the IP address does not. When an internet address is known, ARP is used to determine the node's MAC address.
RARP
- Reverse Address Resolution Protocol is known as RARP.
- The host broadcasts the RARP inquiry packet containing its physical address to the whole network if it wishes to know its IP address. The host IP address is returned in response once a RARP server on the network recognises the RARP packet.
- Reverse Address Resolution Protocol is the name of the protocol used to get an IP address from a server.
- The RARP protocol's message structure is comparable to that of the ARP protocol. Similar to an ARP frame, a RARP frame is transmitted from one machine to another enclosed in a frame's data.
ICMP
- Internet Control Message Protocol is what it's called. In order to notify the sender of IP datagram issues, hosts and routers employ the ICMP protocol at the network layer.
- To determine if the destination is accessible and responding, ICMP performs an echo test/reply.
- Although ICMP can accept both control and error messages, its primary job is to report errors rather than fix them.
- An IP datagram has the source and destination addresses, but it is unaware of the address of the last router it has travelled through. Because of this, ICMP can only communicate with the source and not the nearby routers.
- The sender receives the error messages using the ICMP protocol. Errors are returned to user processes as a result of ICMP packets.
- IP datagrams are used to convey ICMP messages.
- Internet Group Message Protocol is known as IGMP.
- Two modes of communication are supported by the IP protocol:
- A communication method known as "unicasting" has only one sender and one recipient. We may thus define it as one-to-one communication.
- Multicasting: On occasion, the sender desires to deliver the same message to several recipients at once. Multicasting, which uses one-to-many communication, is the name of this method.
- The hosts and router both utilise the IGMP protocol to facilitate multicasting.
- The hosts and router utilise the IGMP protocol to identify the hosts in a LAN that are a part of a group.
- The Internet Protocol (IP) is a protocol, or collection of guidelines, for addressing and routing data packets so they may move between networks and reach their intended location. The Internet divides data into smaller units known as packets for transmission.
- Each packet contains IP information, which enables routers to transmit packets to the appropriate location.
- Every device or domain that connects to the Internet is given an IP address, and data gets to the right place when packets are sent to the IP address associated with them.
- Depending on whatever transport protocol is used with IP, the packets are treated differently once they reach their destination.
Network Access Layer
- The TCP/IP protocol hierarchy's Network Access tier is the bottom tier.
- The protocols in this layer give the system the tools to send data to the other gadgets on a network to which it is directly connected. It specifies how to send an IP datagram over the network.
- In contrast to higher-level protocols, Network Access Layer protocols need to be aware of the specifics of the underlying network (its addressing, packet structure, etc.) to format the data being transferred in a way that complies with network requirements.
- All of the operations performed by the Data Link and Physical layers at the bottom of the OSI reference model can be included in the TCP/IP Network Access Layer.
Ethernet
- Local area networks are generally built using Ethernet, a common communication protocol. Through wires, it sends and receives data.
- This makes it easier to communicate over a network using two or more distinct types of connections, such as copper to fibre optic and the other way around.
Ethernet Types
- Fast Ethernet: This type of internet can send and receive data at speeds of up to 100 Mbps. Twisted pair or CAT5 cable is typically used to support this sort of network.
- Gigabit Ethernet: This kind of network transmits data at a rate of roughly 1000 Mbps or 1Gbps, which is even faster. Fast Ethernet is being replaced with Gigabit speed, which is an improvement. The data transfer speed in this kind of network is influenced by each of the four pairs in the twisted pair cable.
- A 10 Gigabit/second data transfer rate makes 10-Gigabit Ethernet an even more sophisticated and fast network type. This network area can be expanded up to around 10,000 metres by employing a fibre optic connection.
- Ethernet switch: This network type needs a switch or hub. Additionally, a standard network cable is utilised in this instance rather than a twisted pair wire.
IP Adress
- An Internet-connected device or domain is allocated an IP address, which is a distinctive identification.
- Every IP address consists of a string of characters, such "192.168.1.1." Users may visit websites without memorising this long string of characters thanks to DNS resolvers, which convert human-readable domain names into IP addresses.
- Similar to how both the destination address and the return address are contained on a piece of mail, each IP packet will carry both the IP address of the device or domain delivering the packet and the IP address of the intended receiver.
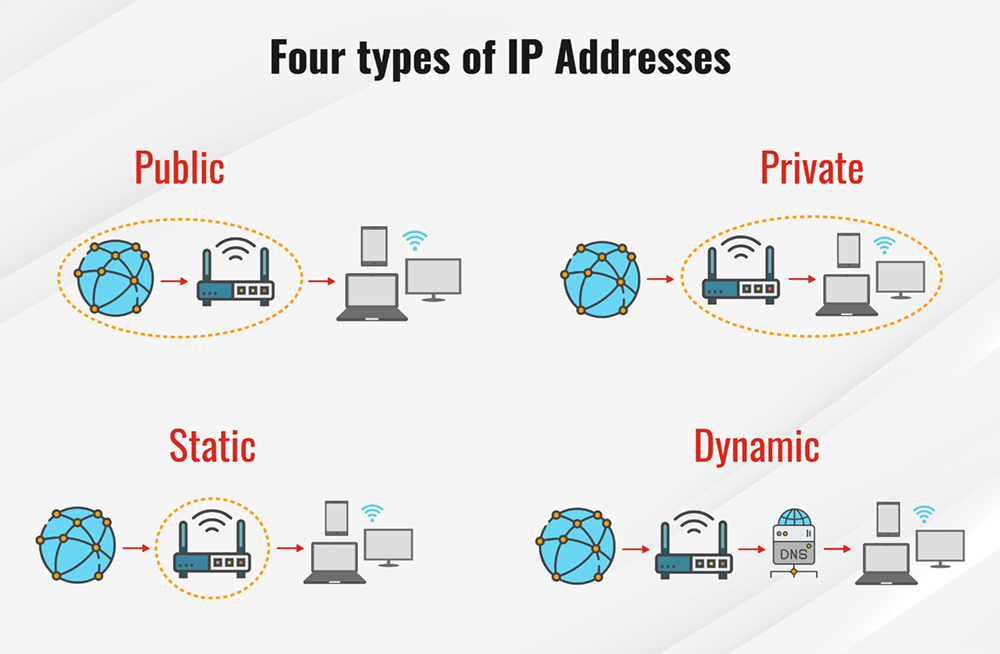
- IP addresses come in four varieties: public, private, static, and dynamic.
- Static and dynamic signify permanence, whereas public and private indicate the location of the network (private is used inside the network, and public is used outside the network).
- An IP address that is static was manually generated rather than being allocated. A static IP address is also permanent, in contrast to a dynamic IP address, which is given by a DHCP server and is susceptible to change.
- The most typical kind of internet protocol addresses are dynamic IP addresses. Unlike static IP addresses, dynamic IP addresses have a limited lifespan and eventually expire. Either the machine will automatically request a new lease or a new IP address might be assigned to it.
Version of IP Address
- Class A, B, C, D, and E are the five IP address classes that TCP/IP specifies. There is a range of legal IP addresses for each class.
- The class is determined by the first octet's value.
- Host addresses may be created using IP addresses from the first three classes (A, B, and C).
- Class D is used for multicast, and class E is utilised for experimental reasons. The other two classes are used for different things.
- Class A IP address has the first octet starting from 0.
- Class B starts from 0+128 = 128.
- Class C starts from 0+128+64=192.
- Class D starts from 0+128+64+32=224.
- Class E starts from 0+128+64+32+16=240.
- Class A ends at 127, which can be inferred from the starting end of Class B.
- Similarly Class B ends at 191.
- Class C ends at 223.
- Class D at 239.
- Class E at 255.
Subnetting
- The process of conceptually dividing a single physical network into several smaller sub-networks or subnets is known as subnetting.
- The client or host address and the server or network address are the two halves of any device's IP address. IP addresses can either be set manually (static IP addresses) or by a DHCP server.
- The subnet mask separates the IP address into host and network addresses, indicating which portions belong to the device and which portions belong to the network.
- Local devices are connected to other networks through the equipment known as a gateway or default gateway. This implies that a local device must submit its packets to the gateway before they may be forwarded to their intended recipient outside of the local network when it wishes to communicate information to a device with an IP address on another network.
Subnet Mask
- On an IP network, a single device is uniquely identified by its 32-bit IP address. The subnet mask divides the 32 binary bits into host and network portions, but they are also separated into four 8-bit octets.
- A broadcast address is always associated with the "255" address, while a network address is always associated with the "0" address. Both are set aside for these specific uses, hence neither may be allocated to hosts.
- Most networks employ the Internet Protocol as the underlying framework to enable device communication, which is made up of the IP address, subnet mask, and gateway or router.
- Subnetting further separates the host part of the IP address into a subnet when organisations want more subnetworking. Subnet masks just serve to make the subnetting process possible.
Classful Routing
- Subnet masks are not imported by Classful Routing. Subnet mask is also given in this case following the route modification.
- A technique of allocating IP addresses called classful addressing divides addresses into five main categories.
- The above image demonstrates how the subnet mask in classful routing is constant across all devices and does not change.
- Variable Length Subnet Mask (VLSM) and Classless Inter-Domain Routing (CIDR) are not supported in Classful Routing.
Classless Routing
- In order to slow down the fast expiration of IP addresses, classless addressing will eventually take the place of classful addressing.
- Subnet mask is imported by classless routing, which makes use of triggered updates. VLSM (Variable Length Subnet Mask) and CIDR (Classless Inter-Domain Routing) are supported in classless routing.
- Hello messages are used for status checks in classless routing. In classless routing, subnet masks may not always be the same for all devices; we can see this in the example image.
Variable Length Subnet Mask(VLSM)
- In VLSM, the subnet design employs several masks inside a single network, i.e., multiple masks are utilised for various subnets within a single class A, class B, or network.
- Due of the varying size of subnets, it is utilised to make them more usable. Additionally, it is described as the procedure of subnetting a subnet.











No comments:
Post a Comment